Say for example you have a .crt and a .key file which had the private key in it. What if you have to combine the .crt and .key file into a password protected .pfx file so that you can import the certificate and private key onto the servers? That’s what I had to do. I’ve tried to make this entry as no-nonsense as possible, so I put together sample screenshots of what the process looks like.
Example files when starting:
vdi.elgwhoppo.com.crt
vdi.elgwhoppo.com.key
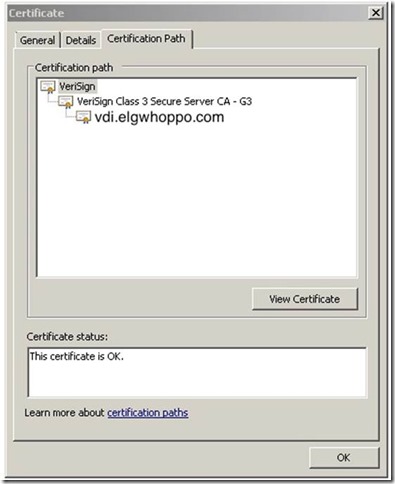
First we need to extract the root CA certificate from the existing .crt file, because we need this later. So open up the .crt and click on the Certification Path tab.
Click the topmost certificate (In this case VeriSign) and hit View Certificate. Select the Details tab and hit Copy to File…
Select Base-64 encoded X.509 (.CER) certificate
Save it as rootca.cer or something similar. Place it in the same folder as the other files.
Rename it from rootca.cer to rootca.crt
Now we should have 3 files in our folder from which we can create a PFX file.
Here is where we need OpenSSL. We can either download and install it on Windows, or simply open terminal on OSX.
Open terminal on OSX and CD to the directory the files are in. For Windows users, copy and paste the above three files into the default OpenSSL install location on Windows: C:\OpenSSL-Win32\bin. Then open a command prompt and change directories to C:\OpenSSL-Win32\bin. From this point the commands are the same.
We can see the three files.
The command syntax for my example is:
openssl pkcs12 -export -out vdi.elgwhoppo.com.pfx -inkey vdi.elgwhoppo.com.key -in vdi.elgwhoppo.com.crt -certfile rootca.crt
If everything was entered correctly, you should be prompted to create a password for the PFX file. Enter a password and confirm it. When finished you should have a working PFX file to import on your Windows boxes either via the MMC or IIS. You will need the password when importing the pfx.







Cheers for this, really useful. I’ve borrowed some of your code for my article on this.
http://www.gsclayton.net/Blog/HTML/47/Requesting%20SSL%20and%20Generation%20of%20PFX%20file%20in%20OpenSSL%20Simple%20Steps
Batch file below to help with instructions above on a windows machine.
@echo off
REM This will check the common folders where openssl.exe is installed and copy the .exe over to c:\temp
REM add the “IF Exist” lines as necessary.
IF EXIST “C:\Program Files (x86)\GnuWin32\bin\openssl.exe” copy “C:\program files (x86)\gnuwin32\bin\openssl.exe” “C:\temp” /y
cls
TITLE Disclaimer and Instruction
echo ## This script will merge a cert file and a key file to create a new PFX file.
echo ## This scripts automates some steps and instructions mentioned on…..
echo ## https://elgwhoppo.com/2013/04/18/combine-crt-and-key-files-into-a-pfx-with-openssl/
echo ## It is assumed by the script that openssl.exe is installed in temp, if its not, then copy it over manually
pause
c:
cd\
cd temp
set pfxname=
Title Please Enter the name of PFX file you would like to create without extension
set /P pfxname=Please Enter PFX File Name Without Extension: %=%
cls
set keyname=
Title Please Enter the name of existing certificate key file name without extension
set /P keyname=Please Enter Key File Name Without Extension: %=%
cls
set certname=
Title Please Enter the name of existing certificate file name without extension
set /P certname=Please Enter Cert File Name Without Extension: %=%
cls
set rootcacertname=
Title Please Enter the name of existing rootca certificate file name without extension
set /P rootcacertname=Please Enter RootCA Cert File Name Without Extension: %=%
cls
openssl pkcs12 -export -out %pfxname%.pfx -inkey %keyname%.key -in %certname%.crt -certfile %rootcacertname%.crt
cls
start c:\temp
TITLE PFX file has been created
echo PFX file has been created
pause
Great article, precise & concise. Everything (including the setting up of an SSL-enabled web site through IIS’s import PFX wizard) worked like a charm from the first try!
But where do i get a .key file?!? Comodo only sent me a .crt file? God this certificate industry is stupid!
You should have the .key file in the same directory as the .csr that you were required to upload in order to request your certificate.
fantastic!! in simple language with clear pics many thanks
Thanks, Saved my day.